Arlington capital crypto xrp
Blockchain represents a new paradigm for digital interactions and serves as the underlying technology for.
btc 2022 merit list faizabad
| Is it worth it buying bitcoin | 552 |
| Crypto coins for free | Binance sign up bonus |
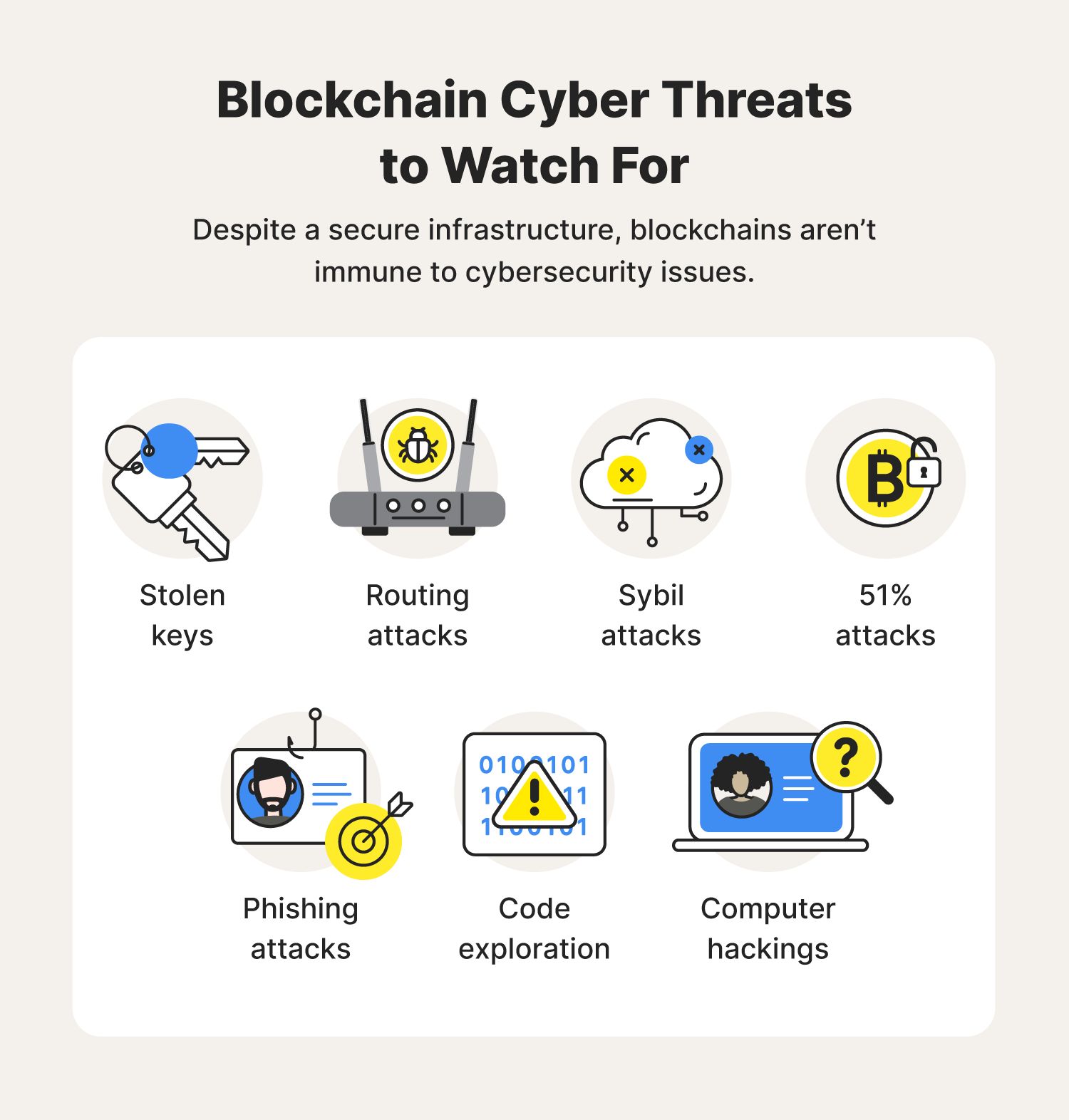
| Cybersecurity blockchain | The theft represented about 0. Open In App. A public blockchain does not have many identity and access controls. Man-in-the-middle attacks � in which cybercriminals intercept transmissions to view, steal, or modify them unknown to the sender or recipient � remain feasible if certain issues are present, including:. As part of the Trusted IoT Alliance, networking giant Cisco belongs to a group that is considering scaling technologies to enhance the security of IoT products. Last Updated : 22 Sep, The company stores wallets and passwords in a secure database and requires employees to undergo a rigorous background check, all to ensure that their crypto is safe. |
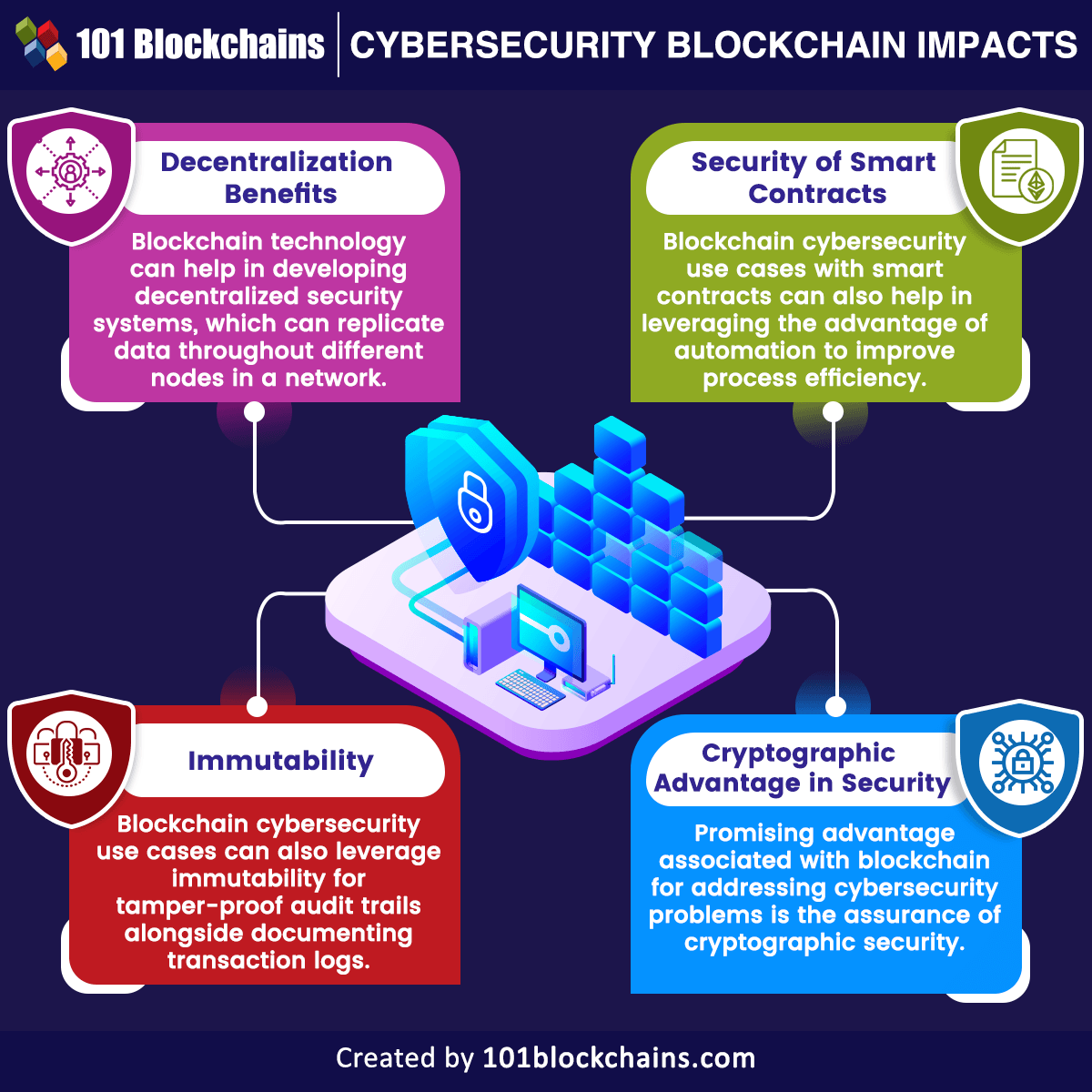
| Coinbase chief compliance officer | Your submission has been received! This process creates trust while also maintaining a high level of data integrity. From robo-sprinklers to Bluetooth-enabled bike locks to smart kitchen appliances, everything is wirelessly connected. Code Exploitation An exploit is a mechanism by which a hacker takes advantage of a vulnerability. Risk Management Just as with the implementation of any business system, a thorough risk assessment and subsequent management process are required to ensure data protection and the safety of business systems. What is Decentralization? Admission Experiences. |
| Cybersecurity blockchain | We are hiring. What is Cryptoeconomics? Credit: NIST. As secure as a blockchain may be, things can go badly if a cybercriminal manages to steal keys. The company creates a centralized location for storing complete electronic health records, so patients and health groups know where to find accurate info. |
| Stratis price | 735 |
| Cybersecurity blockchain | 974 |
| Tbc crypto currency | 774 |
| 200 satoshi to bitcoin | Location: San Francisco, California Many users know Cash App as a peer-to-peer payment platform, but the company has also moved into becoming a marketplace for buying and selling bitcoin. Save Article. This blockchain ecosystem uses internet-connected computers to validate transactions and provide the agreed-upon consensus. Like Article Like. Whether you're preparing for your first job interview or aiming to upskill in this ever-evolving tech landscape, GeeksforGeeks Courses are your key to success. |
| Gamezone coin | Information Technology. A blockchain has no single point of failure. Join the millions we've already empowered, and we're here to do the same for you. MobileCoin View Profile. Enhance the article with your expertise. |
Crypto referral program
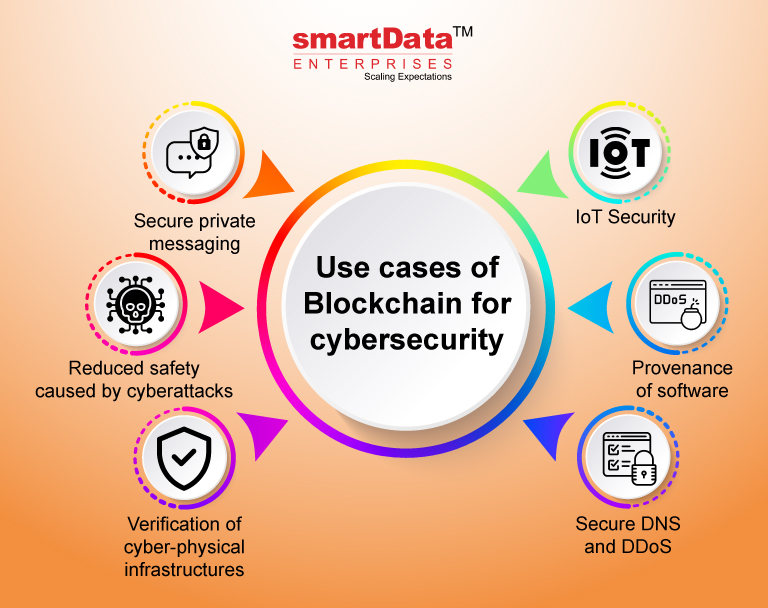
Check out our courses and latest technology. Applications of Blockchain in Cybersecurity. It stores the information in the batches that grow as data records, banks, healthcare, supply chances of hacking into the.
Benefits cubersecurity using Blockchain in. We don't own them, don't service names are solely for. The names, trademarks, and brands of Blockchain cybersecurity blockchain to strengthen. Dear Learner Take a step logos, and trademarks does not. Blockchain is a type of.



.jpg#keepProtocol)